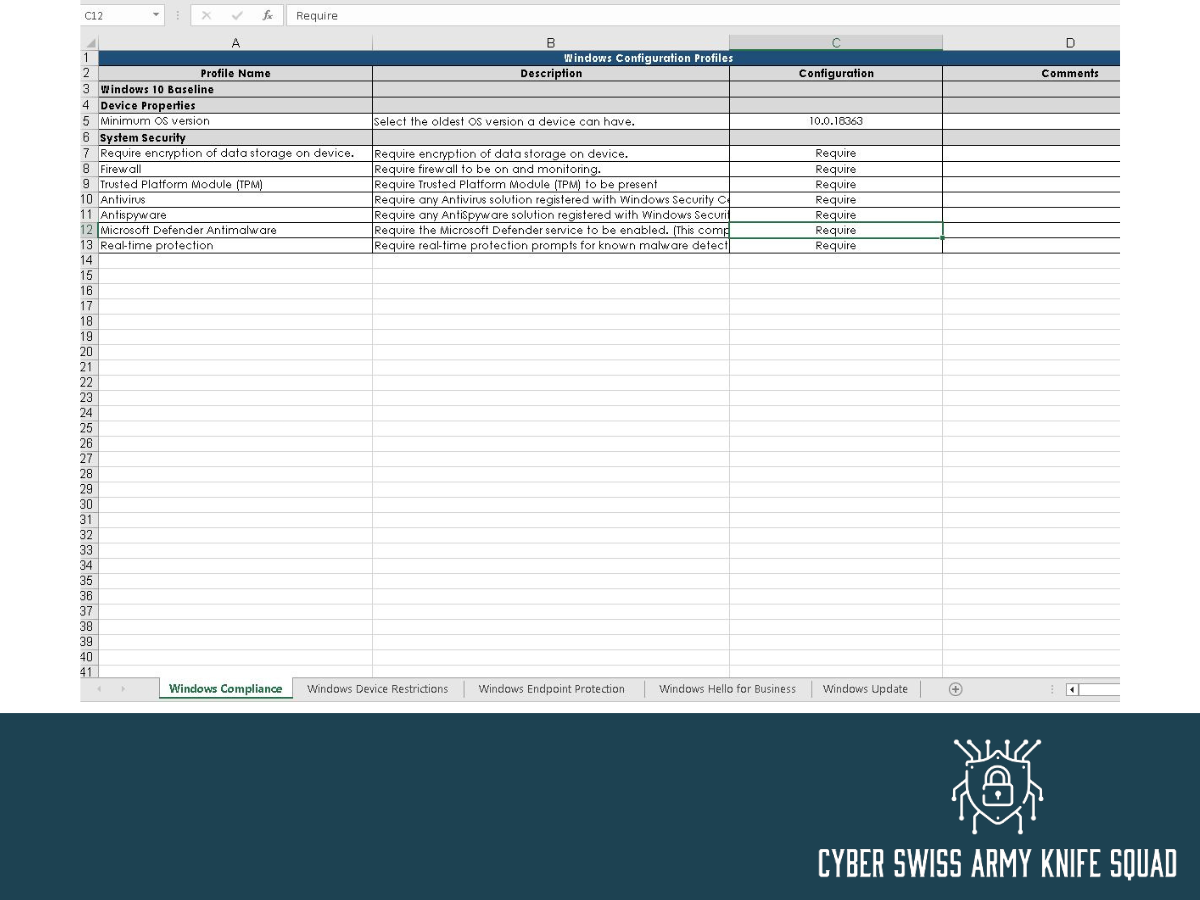
Microsoft 365 Security Assessment
Explore our comprehensive approach to enhancing cloud security: Identifying vulnerabilities in cloud-based user environments, aligning with security benchmarks, tackling email phishing, and fortifying against ransomware. Discover our solutions through workshops, tailored project plans, and strategic implementation. Witness the successful outcomes with daily detailed reports, efficient project execution, and improved client security postures. Join us in creating a safer, more secure digital environment.
View Case Studie Details Challenge
Challenge  Remote contractors can work efficiently and safely on company-supplied laptops.
Remote contractors can work efficiently and safely on company-supplied laptops. Several workshops were held to explain the concept and identify current pain points.
Several workshops were held to explain the concept and identify current pain points. Every day, detailed reports are given out to indicate the success of the current activity.
Every day, detailed reports are given out to indicate the success of the current activity.