Implementing Microsoft Intune and Microsoft Defender For Endpoint
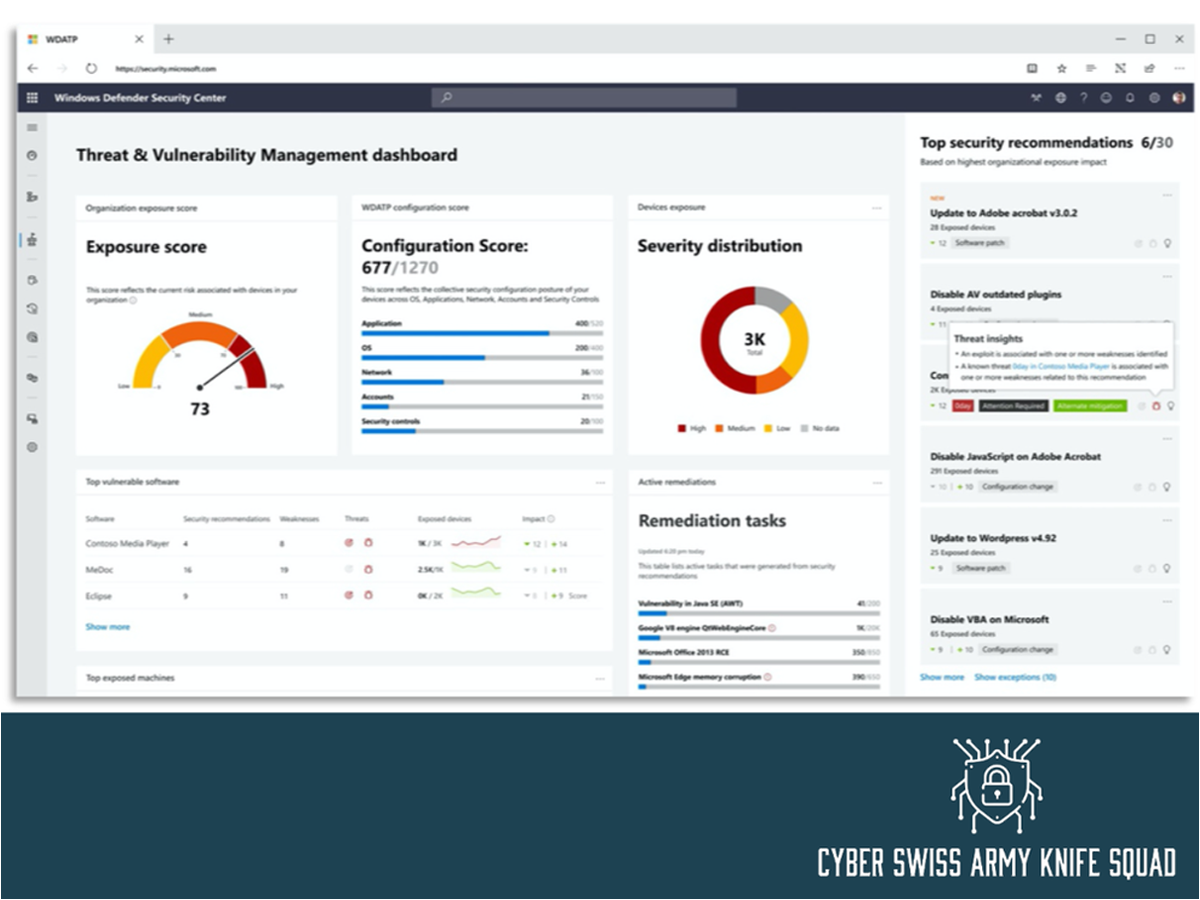
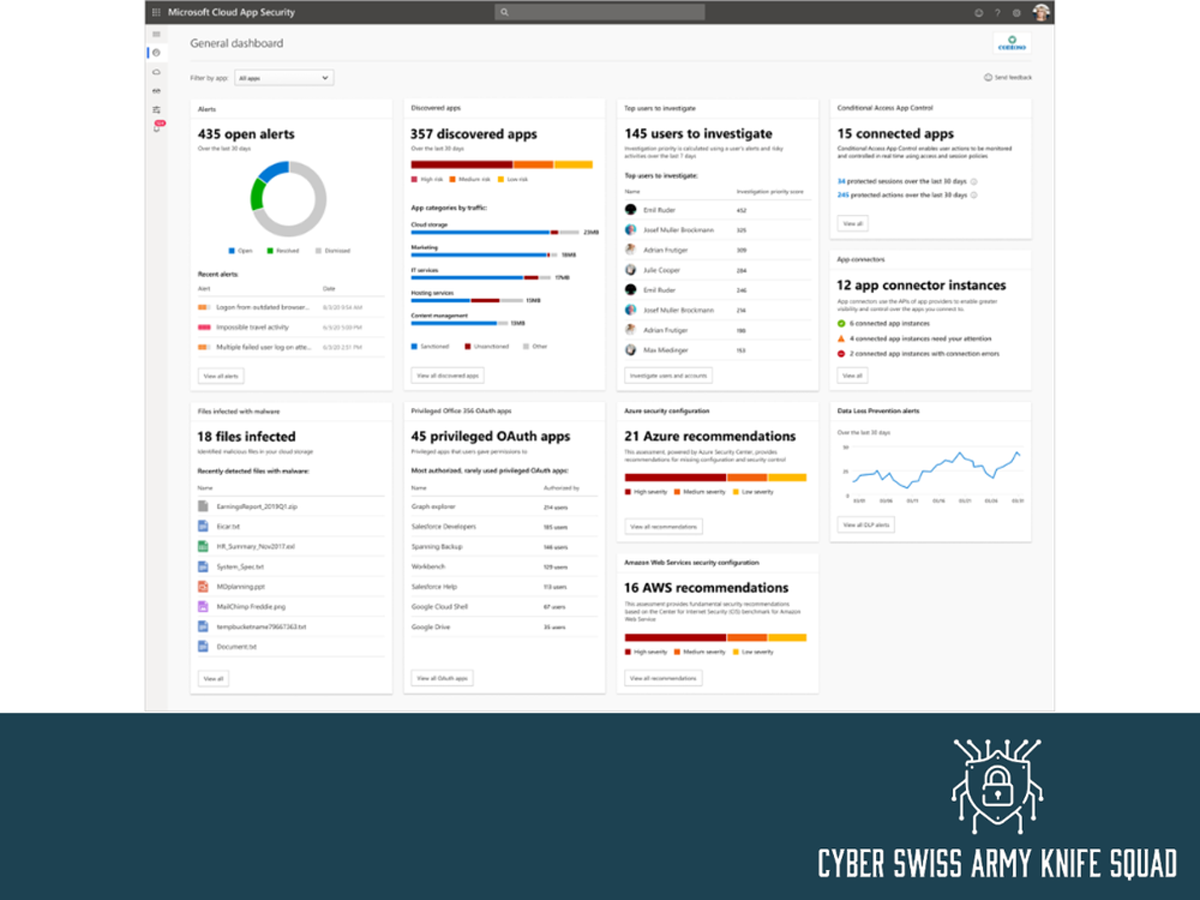
Discover how remote contractors can work efficiently with company laptops, manage a vast array of devices without a server, and protect against ransomware. Learn about our solution process from workshops to execution, achieving 100% device coverage across all platforms, and delivering ahead of schedule. Explore our comprehensive approach to managing Windows, iOS, and Android platforms, ensuring up-to-date, secure, and efficient remote working environments.
View Case Studie Details